Safe Stadiums
Explore integrated stadium security technology designed to ensure stadium safety from initial detection to final response across your entire perimeter
The Motorola Safety Reimagined Platform for Stadiums from Arkansas Valley Communications
Keep Up With The Speed Of Technology On One Unified Platform
From sporting events to live concerts, the world’s stadiums host millions of visitors each and every year. Creating a positive and secure visitor experience while maintaining efficient, streamlined operations is the promise stadiums make. But delivering on this promise is only achievable with a foundation of safety. Everything starts with safety. It’s the center that holds stadium operations together.
The Motorola Solutions Safety Reimagined Platform unifies voice, video, data, and analytics technologies on one platform. With Safety Reimagined you can increase security, improve safety, reduce costs, boost efficiency, and improve communications across staff, teams, and locations. These solutions are designed with our customers’ needs at their core; helping Arkansas Valley Communications deliver on our promise of creating a safer world.

Safety Reimagined – The Next Generation of Smart Technologies
Improve Safety and Operations on One Platform
Leveraging Motorola’s Safety Reimagined Platform allows your day-to-day operations and emergency situations to be more manageable and measurable for predictable outcomes and optimizations.
Select a use case below and explore
The Safety Reimagined integrated technology ecosystem can provide meaningful outcomes to help ensure stadium safety
Escalated fan interaction
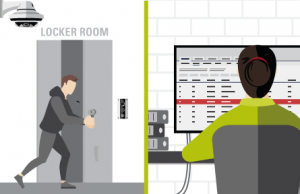
Disruptive fan reported. A staff interacts with a disruptive individual and activates their body-worn camera. An alert is automatically sent to appropriate staff directly on their radios and in the command center.

Situational intelligence gathered. The operational command center receives the alert and all relevant camera feeds are populated and body worn camera footage is live streamed. Other nearby security resource locations are identified.

Resources dispatched. Security teams are dispatched to the situation and receive intelligence including an image of the disruptive guest prior to their arrival on scene.

Situation contained and mitigated. The individual is escorted off the premises and an incident report is then securely documented with all relevant data.
Banned individual
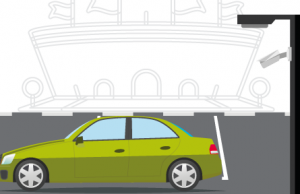
Known person identified. A banned individual’s license plate is recognized entering the stadium parking lot. An alert is automatically sent to stadium operations directly on their device of choice and in the command center.

Situational intelligence gathered. Cameras within relevant parking area populated and the closest security personnel are identified.

Notification communicated. Security staff are notified of the situation and an image of the banned individual is sent to prevent entry.

Incident managed and reported. Stadium operations monitor the situation via fixed video and live streaming body worn cameras. An incident report is logged with pre-populated fields and relevant data.
Concealed weapon detection
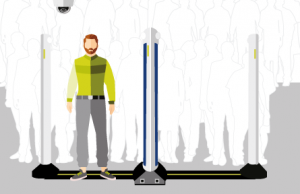
Concealed weapon detected. Evolv Express detects the presence of a concealed weapon on a person entering a stadium.

Fleeing individual monitored. The threat is confirmed and an alert is issued to ACC to notify central security operators. Cameras onboard the towers simultaneously stream video to ACC.

Resources dispatched. An alert is automatically issued from ACC to nearby devices to notify additional security operators. Suspect’s details and location is shared with additional security operators across the stadium.

Incident managed and reported. The suspect makes a run for it and security operators track their location within the stadium. The incident is then securely logged with pre-populated fields and relevant data.
Restricted area access
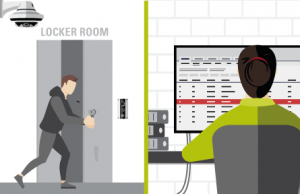
Forced entry recognized. Alert is sent to security operations center and personnel of a forced entry into a player locker room area.

Situational intelligence gathered. Nearby cameras are populated and the closest security personnel are identified.

Notification communicated. After the initial radio alert, intruder image and location sent to nearby security teams in the field. Anticipated escape route determined and security directed to intercept.

Incident managed and reported. Public safety is notified and security apprehends intruder while wearing body-worn cameras. The incident is logged with pre-populated fields and relevant data.
Lost or missing individual

Lost person reported. A person is reported lost by a companion to a nearby security officer or employee. An image of the child is provided and shared with appropriate staff.

Search initiated with video analytics. Using the provided image of the individual, security teams can leverage the child’s appearance, shoes, or clothing, etc. as identifying characteristic to begin an area search using video analytics.
Intelligence shared with field. Using two-way radios, security teams are notified on where to begin the search. The image of the child is broadcasted to the security team and updates are continuously provided to relevant teams.

Situation resolved and documented. The lost individual is located and returned to their guardian. An incident report is securely documented with all relevant information.
Learn How Safety Reimagined Can Help Your Operations
Safety Reimagined Voice, Video, Data, And Coordination Solutions from Arkansas Valley Communications
Improve Safety And Security with a Coordinated Solution
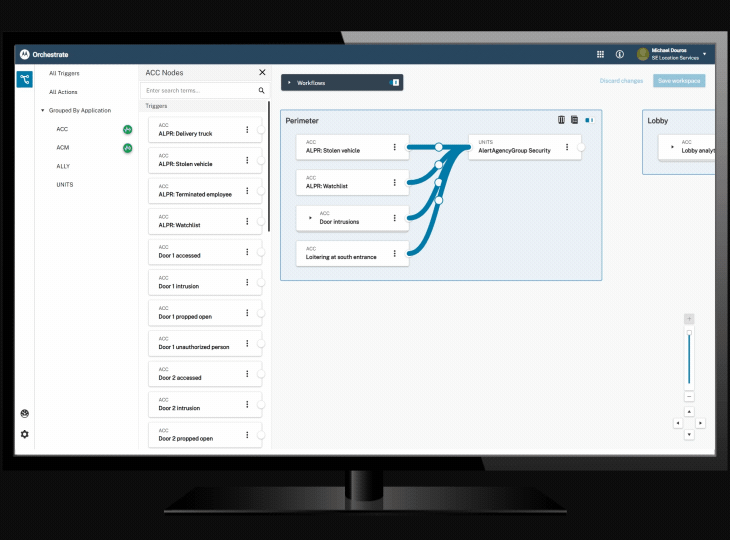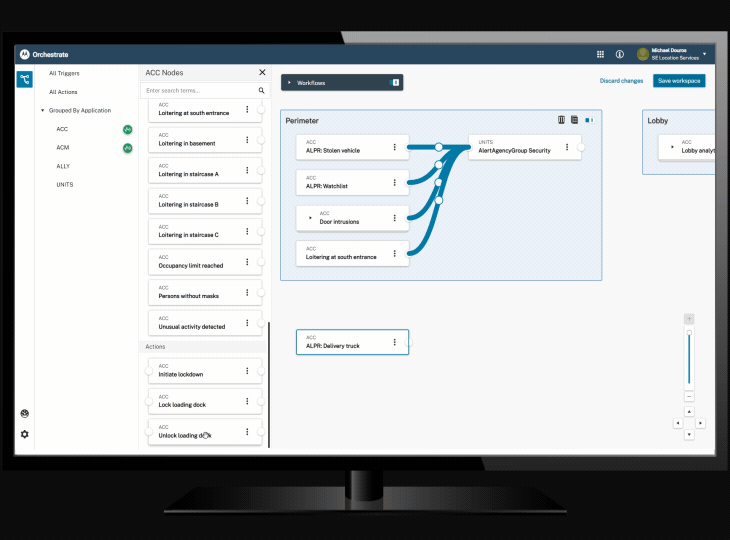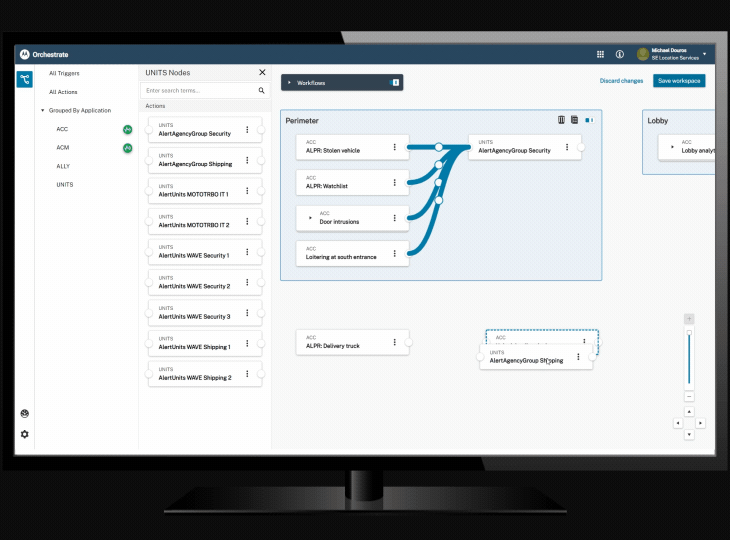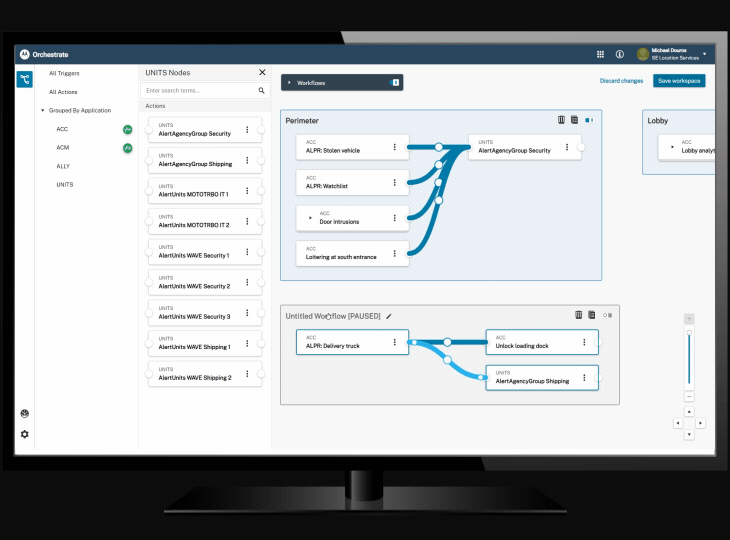
Orchestrate workflow automation tool