Solving For Safer: Safer Hospitals
Explore hospital security technology designed to ensure safety and efficiency ranging from initial detection to final response across the Arkansas Region operations
The Motorola Safety & Security Ecosystem for Hospitals from Arkansas Valley Communications
Safety And Collaboration During Healthcare's Vital Moments
There are countless reasons an individual could be entering a healthcare facility. Whether they are a patient, a healthcare worker, security staff or custodian their experience should begin with safety. We envision a world where technology works seamlessly together to combine intelligent awareness solutions with fast, seamless communication to enable not only safety but efficiency, from intake to discharge. We call this vision the Motorola Solutions Safety & Security Ecosystem—a reimagined approach to safety.
The Motorola Solutions Safety & Security Ecosystem unifies voice, video, data, and analytics technologies on one platform. With the Safety & Security Ecosystem, you can increase security, improve safety, reduce costs, boost efficiency, and improve communications across staff, teams, and locations. These solutions are designed with our customers’ needs at their core; helping Arkansas Valley Communications deliver on our promise of creating a safer world.

Select a use case below and explore
The Safety & Security Ecosystem integrated technology can provide meaningful outcomes to help ensure hospital security and efficiency
ER Waiting Room Incident
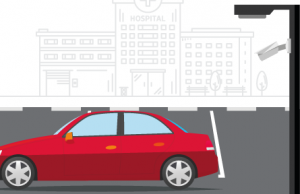
Unusual speed recognized. Erratic driving detected in the parking lot outside of ER and security is alerted and relevant cameras are automatically populated.

Situation monitored. Security monitors all relevant cameras and views individual exit the car with a weapon drawn as they approach the ER entrance.

Notification communicated. Alert sent across radios and smartphones to inform all relevant security teams of the situation with image of intruder.

First response dispatched. Security teams approach area wearing body-worn cameras and local police directly engaged. Incident logged with pre-populated fields and relevant data.
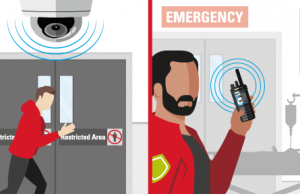
Propped or forced door
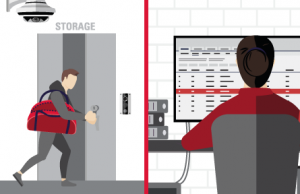
Access control breach recognized. Forced entry detected in sensitive area and an alert is automatically sent to appropriate staff on their device of choice.

Movements monitored. Relevant cameras instantly populate and intruder is identified and monitored through facility using their appearance. Location of nearest security resources determined.
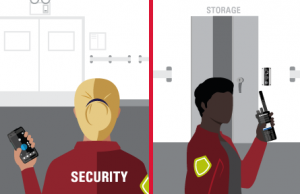
Notification communicated. Resources are dispatched with image and location of individual.

First response dispatched and incident documented. Security teams approach area wearing body-worn cameras and local police directly engaged. Incident logged with pre-populated fields and relevant data.
Be on the lookout (BOLO)
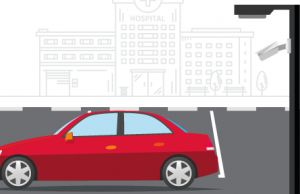
License plate recognized. The license plate of an ex-employee is detected entering hospital grounds. An alert is automatically sent to appropriate staff on their device of choice and to the command center.

Appearance detected. Using a watch list, the intruder is automatically located approaching the hospital and identified. Security receives a notification every time the intruder comes into view of a camera.
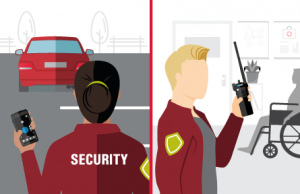
Notification communicated. Nearest security resources dispatched with location and images of the unwelcome individual.

First response dispatched and incident documented. Security teams approach the intruder wearing body-worn cameras and local police directly engaged. Incident logged with pre-populated fields and relevant data.
Off-hours presence detection
Presence detected during off-hours. Video analytics detect the presence of an individual in a sensitive area during off-hours. An alert is automatically sent to appropriate staff on the device of their choice and to the command center.

Situational awareness gathered. In the command center, nearby cameras are populated and closest response resources are determined using GPS location data.
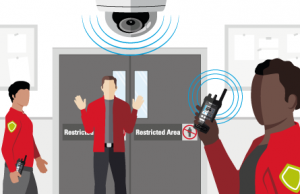
Resources dispatched. Appropriate individuals are dispatched to the area with image of the intruder and other multimedia intelligence.

Situation resolved. The passenger is discreetly isolated and a medical screening is conducted and an incident report is automatically logged.
Patient elopement
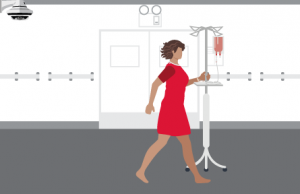
Missing patient reported. A hospital staff member notifies security of a missing, at-risk patient.

Appearance search on cameras. Security uses a description of the patient to automatically search all cameras to track movement and determine their location.
Teams coordinated. Closest security officer or hospital staff to the patient is determined and dispatched to retrieve the patient with image and location information.

Incident recorded. Hospital security wearing body-worn cameras render the patient safe in a timely manner and an incident report is securely logged.
Learn How The Safety & Security Ecosystem Can Help Your Operations
Safety & Security Ecosystem Solutions from Arkansas Valley Communications
Integrated technologies crafted to enhance safety everywhere
Critical Communications
Command Center
Video Security
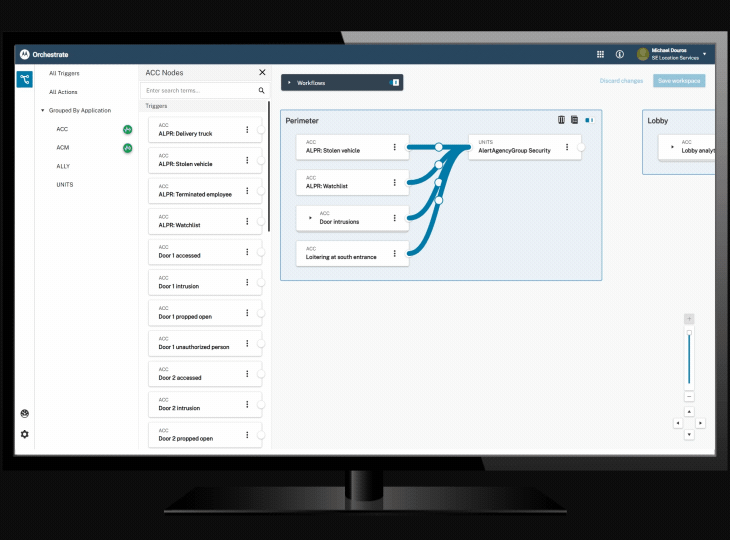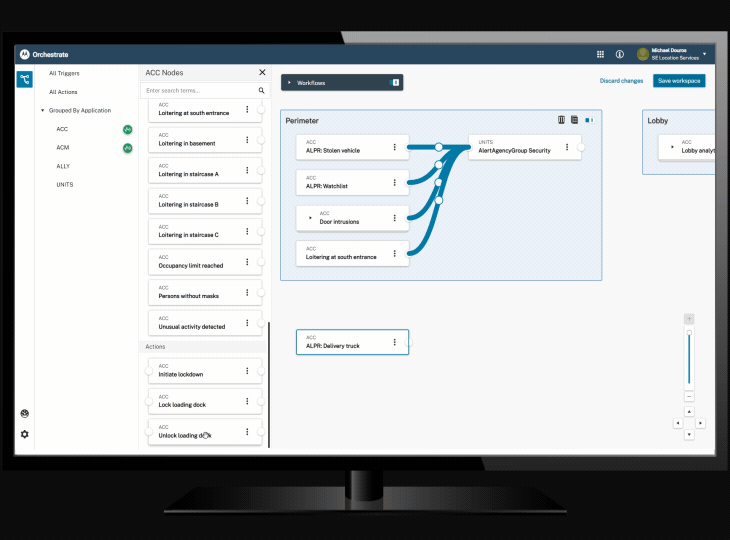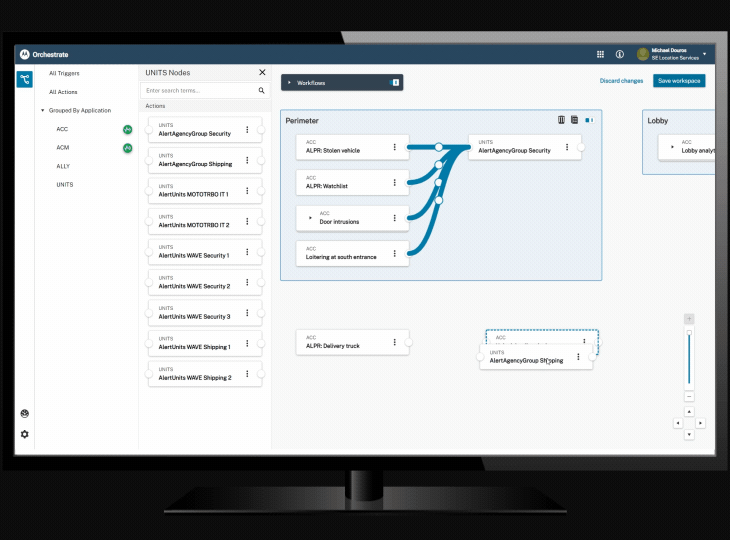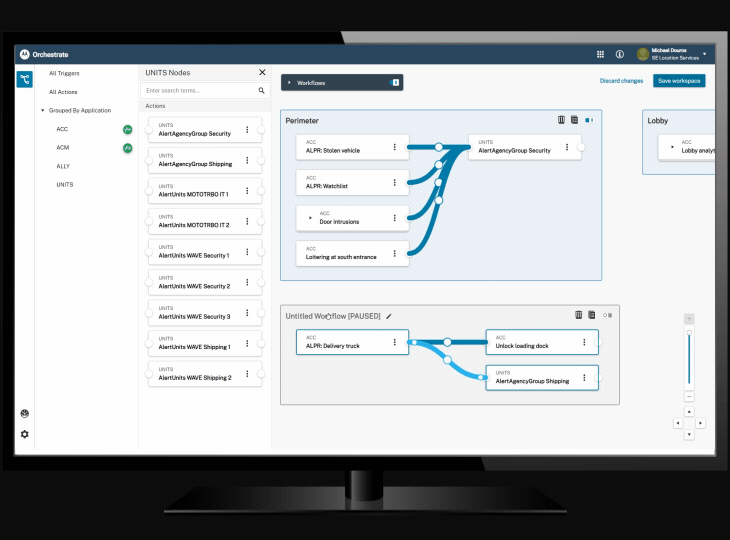
Orchestrate workflow automation tool