Safe Manufacturing
Explore integrated technology designed to ensure manufacturing plant safety ranging from initial detection to final response across the Arkansas Region facilities
The Motorola Safety Reimagined Platform for Manufacturing from Arkansas Valley Communications
Driving Production Forward With Smart, Integrated Technologies
Today, modern manufacturers are continually tasked with optimizing operations, ensuring uptime and maintaining visibility throughout production. The push toward smart manufacturing and Industry 4.0 is introducing increased connectivity and automation throughout the daily workflow in order to produce quality products while reducing costs and minimizing downtime. Organizations are looking to accelerate improvements by connecting machines, people, data and value chains throughout their facility. The movement toward “smart” factories can deliver measurable business results and is expected to be the main driver of manufacturing competitiveness in the next five years. And, all of this must come together while ensuring a production environment that is safe and secure for employees, visitors, property and assets.
The Motorola Solutions Safety Reimagined Platform unifies voice, video, data, and analytics technologies on one platform. With Safety Reimagined you can increase security, improve safety, reduce costs, boost efficiency, and improve communications across staff, teams, and locations. These solutions are designed with our customers’ needs at their core; helping Arkansas Valley Communications deliver on our promise of creating a safer world.

Safety Reimagined – The Next Generation of Smart Technologies
Improve Safety and Operations on One Platform
Leveraging Motorola’s Safety Reimagined Platform allows your day-to-day operations and emergency situations to be more manageable and measurable for predictable outcomes and optimizations.
Select a use case below and explore
The Safety Reimagined integrated technology ecosystem can provide meaningful outcomes to help ensure manufacturing plant safety
Propped door / loitering
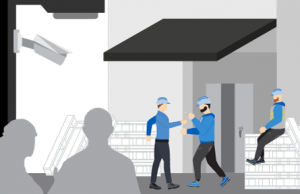
Propped door alert. Alert sent to security about an open door in a restricted area outside of the facility.

Loitering alert. Security alerted to group of individuals loitering outside of propped door entrance.

Notification communicated. After initial alerts, image and location of the individuals are sent to field security teams to disperse the crowd and secure the door.

Corrective action taken. Security locates the loiterers and corrects action and an incident is logged with pre-populated fields and relevant data allowing for further training and analysis.
Machine Monitoring Alerts

Machine alert activated. Machine failure alert on production line automatically triggers an alert to the line supervisor.

Production monitored. Operational staff use cameras to monitor the situation and evaluate how the issue is affecting overall production.

Notification communicated. The line supervisor creates work order ticket for maintenance and communicates directly with the plant manager. An All Call notification is sent to other departments to notify them of an issue.

Issue resolved minimal downtime.
Manufacturers can deploy CBRS networks to power security cameras, connected machines and more with lightning-fast private broadband data, and the coverage, capacity and control your plant needs.
Restricted / Hazardous Area
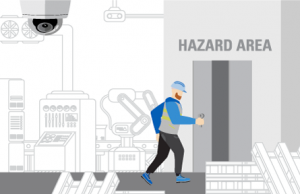
Employee enters monitored area. Employee enters a hazardous area that is monitored with video at all times.

Extended presence recognized. Alarm is triggered when employee presence exceeds the predetermined time limit and Focus of Attention provides exact location.
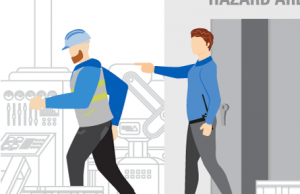
Notification communicated. Ops Center notifies floor supervisor with location information to retrieve employee from the area.
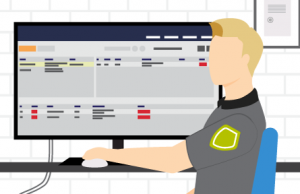
Employee located. Employee is located, and condition confirmed ok. Reports are run weekly to monitor violations and inform for additional training or procedural adjustments.
Be on the lookout (BOLO)
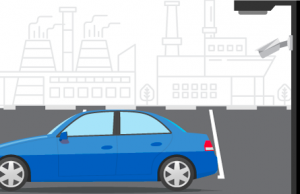
License plate recognized. Using an existing database, an automatic license plate reader recognizes an ex-employee’s vehicle entering the factory parking lot and alerts plant security.

Appearance detected and alert triggered. Using a watch list of known individuals, the individual is automatically located approaching the facility and identified. Security automatically monitors the intruder’s movements.

Notification communicated. Security personnel are notified and dispatched with an image and the location of the intruder. Field security intercepts the individual before reaching the plant entrance.

Incident managed and reported. An incident is logged with pre-populated fields and relevant data.
Fire or substance leak
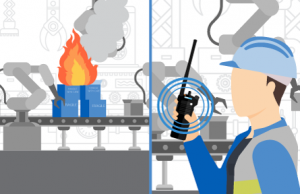
Fire detected. An alarm detects a fire or substance leak and security and operations are automatically alerted on their device of choice and in the command center.

Situation analyzed. Security quickly assesses relevant video for situational awareness and can monitor the plant as employees evacuate based on protocols.

Notification communicated. Response teams are dispatched according to safety protocols. Mass communication sent to all employees to evacuate.

Incident managed and reported. Appropriate authorities and fire teams are engaged. Access Control Manager Verify confirms employee and visitor location during mustering. Incident report logged for future analysis and investigation.
Worker Down
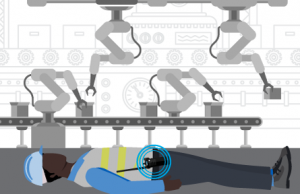
Worker down alert. Man Down feature on radio detects a fallen worker in remote area of the plant and automatically sends an alert over the radio network to security and operations.

Real-time video verification. Control room operator receives the emergency alert, verifies the location of the worker and uses live video to evaluate and monitor the circumstances of the incident.

Notification communicated. Based on defined protocols, the plant emergency response team is dispatched to assist the worker and investigate using real-time location data.

First response dispatched. On-site or local first responders arrive to provide medical attention. An incident is logged with pre-populated fields and relevant data for analysis and claims.
Learn How Safety Reimagined Can Help Your Operations
Safety Reimagined Voice, Video, Data, And Coordination Solutions from Arkansas Valley Communications
Improve Safety And Security with a Coordinated Solution
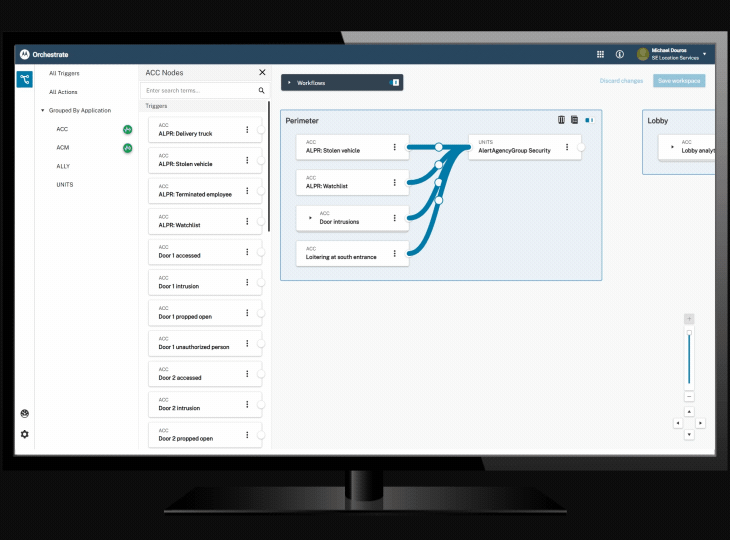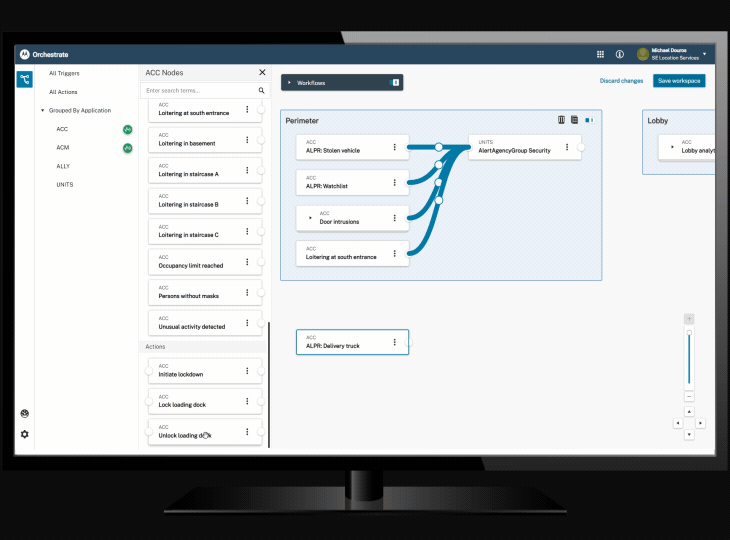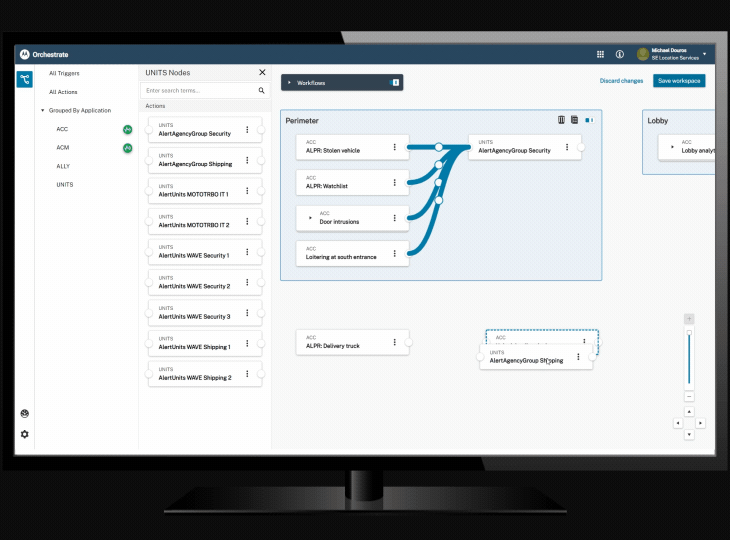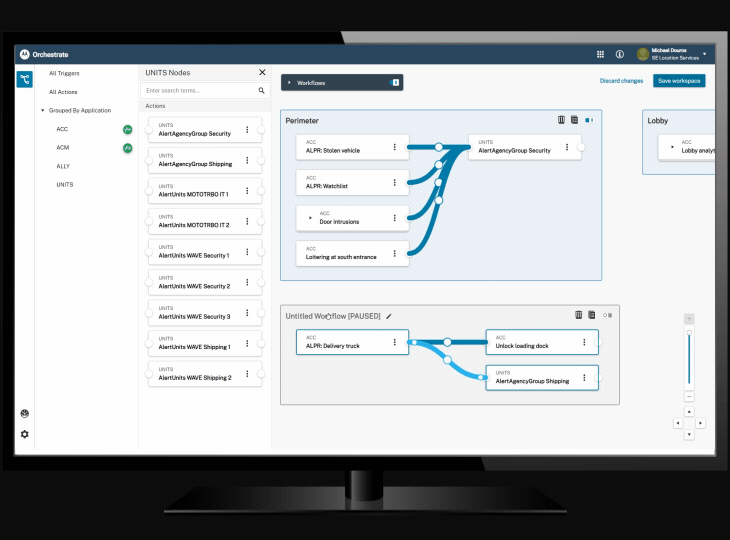
Orchestrate workflow automation tool